Authorization fields
In this final step you have to assign the values required to run the functionalities to the authorization fields of each single object.
RFC access for ZAUDICZ_RFC_READ_TABLE
| Authorization check for RFC access (S_RFC) | |
|---|---|
|
Activity (ACTVT) |
16 (Execute) |
|
Name of RFC object (RFC_NAME) to be protected |
ZAUDICZ_RFC_READ_TABLE |
|
Type of RFC object (RFC_TYPE) to be protected |
FUNC (function module) |
Table: Authorization check for RFC access (S_RFC)

Figure: Authorization check for RFC access (S_RFC)
RFC Access
| Authorization check for RFC access (S_RFC) | |
|---|---|
|
Activity (ACTVT) |
16 (Execute) |
|
Name of RFC object (RFC_NAME) to be protected |
RFC1, SCUST_SYS_INFO, SDIFRUNTIME, SDTX, SLI1, SUSR, SYST |
|
Type of RFC object (RFC_TYPE) to be protected |
FUGR (Function group) |
Table: Authorization check for RFC access (S_RFC)
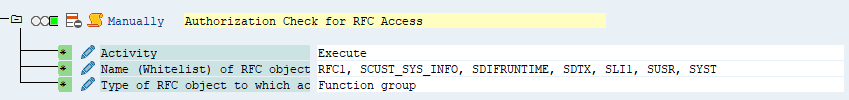
Figure: Authorization check for RFC access (S_RFC)
Note:
The authorizations for the function groups SLI1 and SCUST_SYS_INFO are optional for the download of data, however, for the download of Data Dictionary information these authorizations are required.
The called function modules SCSI_GET_SYSTEM_INFO and SLIC_GET_CUSTKEY provide additional information, which is displayed when testing the connection and which is required to download the Data Dictionary information.
When calling the function modules SLIC_GET_CUSTKEY the additional authorization S_ADMI_FCD and the activity PADM are required for full functionality.
| System authorizations (S_ADMI_FCD) | |
|---|---|
|
Activity (ACTVT) |
PADM (process administration with the transactions SM04, SM50) |
Table: S_ADMI_FCD authorization
If this authorization is missing, no customer key will be returned. Downloading Data Dictionaries, however, will be completed successfully.
Table maintenance
| Table maintenance using default tools like SM30 (S_TABU_DIS) | |
|---|---|
|
Activity (ACTVT) |
03 (Display) |
|
Auth. group (DICBERCLS) |
* |
Table: Table maintenance using default tools like SM30 (S_TABU_DIS)

Figure: Table maintenance using default tools like SM30 (S_TABU_DIS)
Customer specific adjustments
The value "*" for the DICBERCLS authorization field makes sure that the following functions are available:
- Download the Data Dictionaries of the target system.
- Access to an SAP® system using ZAUDICZ_RFC_READ_TABLE.
- Access to data of all available tables of the Data Dictionaries in the SAP® system.
- Export all available/selected table definitions (Data Dictionary).
To create customer specific authorization objects please note:
-
The authorization groups below are required to use the SmartExporter functionality to download Data Dictionaries (see point a):
Table maintenance using default tools like SM30 (S_TABU_DIS) Activity (ACTVT)
03 (Display)
Auth. group (DICBERCLS)
&NC&, SC, SS, STRW
Table: DICBERCLS for table access (S_TABU_DIS) for Data Dictionary download
Note:
With SAP® base version 731 or higher also the authorization group STRW for downloading Data Dictionaries is required because the tables TDEVC and TADIR were assigned anew.
-
The following authorization groups are the minimum configuration essential for the SmartExporter functionalities (see point b and d):
Table maintenance using default tools like SM30 (S_TABU_DIS) Activity (ACTVT)
03 (Display)
Auth. group (DICBERCLS)
&NC&, SS
Table: Minimum configuration of DICBERCLS for table access (S_TABU_DIS)
-
Additionally the corresponding authorization groups for the access of specific tables are to be defined (see section “Customer specific adjustments” - point c above). Refer to the SAP® table TDDAT to get the information for the authorization groups.
Example: Authorization group FB01 to access table T001.
Table maintenance using default tools like SM30 (S_TABU_DIS) Activity (ACTVT)
03 (Display)
Auth. group (DICBERCLS)
&NC&, SS, FB01
Table: Additional definition of DICBERCLS for table access (S_TABU_DIS)
Note:
If you are using SAP® systems with a base release version 700 or higher, a new authorization object S_TABU_NAM is available (please refer to SAP® note 1481950). This object also allows you to restrict the access on table level below or alongside an authorization group.
You can find a list of function modules used by SmartExporter for the access via ZAUDICZ_RFC_READ_TABLE RFC module here.
-
Save the changes by clicking the Save
 icon. Click the Generate
icon. Click the Generate  button to generate the authorization role.
button to generate the authorization role.Now the authorization role Z_SE_ZAUDICZ is defined.

Figure: Activated authorization role Z_SE_ZAUDICZ
Copyright © 2019 Audicon GmbH. All rights reserved.