SmartExporter end user
To call the SmartExporter RFC function modules the user requires the following authorizations.
RFC Access
| Authorizations check for RFC access (S_RFC) | |
|---|---|
|
Activity (ACTVT) |
16 (Execute) |
|
Name of RFC object (RFC_NAME) to be protected |
/AUDIC/SE, RFC1, SDIFRUNTIME, SYST, SCUST_SYS_INFO, SLI1, SDTX, SUSR |
|
Type of RFC object (RFC_TYPE) to be protected |
FUGR (Function group) |
Table: Authorizations check for RFC access (S_RFC)
Note:
When using SAP® 4.6C you have to replace SDIFRUNTIME by SDIF.
The authorizations for the function groups SCUST_SYS_INFO and SLI1 are optional for the download of data. However, for the download of Data Dictionaries these authorizations are required.
If these authorizations are not assigned, not all information can be shown in the connection test of the SmartExporter Windows client.
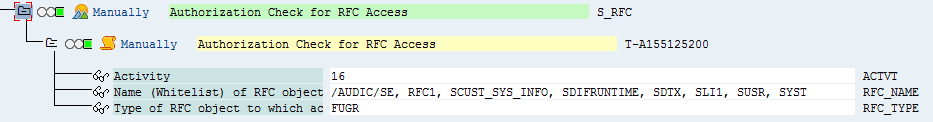
Figure: Authorizations check for RFC access (S_RFC)
| System authorizations (S_ADMI_FCD) | |
|---|---|
|
Process administration with the transactions SM04, SM50 |
PADM |
Table: System administration function (S_ADMI_FCD)
Note:
The authorization process administration S_ADMI_FCD, activity PADM is optional. If this authorization is not assigned, not all information can be shown in the connection test and the Data Dictionary download of the SmartExporter client.

Figure: System administration function (S_ADMI_FCD)
| Archiving (S_ARCHIVE) | |
|---|---|
|
Activity |
03 |
|
Work area |
Not maintained |
|
Archiving Object |
Not maintained |
Table: Archiving (S_ARCHIVE)
Note:
The attributes for the authorization object have to be defined according to your requirements on an individual basis.
To allow access to archived data in an SAP® system, a separate license for the SmartExporter client is required.
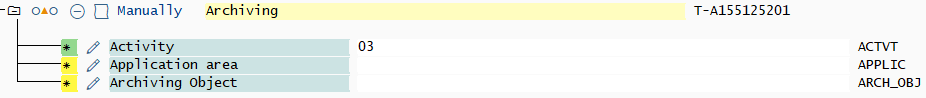
Figure: Archiving
| Batch-Processing: Batch-Jobs (S_BTCH_JOB) | |
|---|---|
|
Job operations |
RELE, SHOW, PROT |
|
Summary of jobs |
* |
Table: Batch-Processing: Batch-Jobs (S_BTCH_JOB)
Note:
Without the authorization to enable one's own batch jobs (RELE) it is not possible to run asynchronous Data Requests or to run a Data Request as a background job.
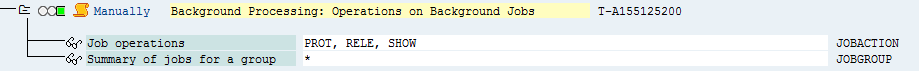
Figure: Batch-Processing: Batch-Jobs (S_BTCH_JOB)
Writing files to the backend file system requires the following authorizations (S_DATASET).
| Authorization for file access (S_DATASET) | |
|---|---|
|
Activity (ACTVT) |
Delete, Read, Write |
|
Physical file name (FILENAME) |
Not maintained |
|
ABAP-Program name (PROGRAM) |
/AUDIC/* |
Table: Authorization for file access (S_DATASET)
Note:
You can further restrict the authorizations using the attributes FILENAME and PROGRAM.
The /AUDIC/* value for the PROGRAM attribute only allows programs, function modules and classes from the AUDIC namespace to access the specified path.
When using the FILENAME attribute for the restriction you have to specify the physical path in the file system of the application server(s). You cannot specify the logical file name which is configured in the SmartExporter settings.
The maximum length of the path of 59 characters may not be exceeded because otherwise no authorization check is possible.
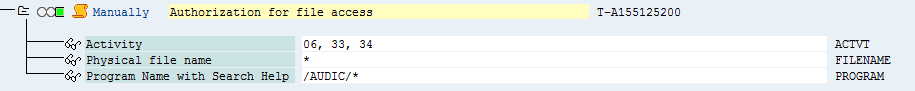
Figure: Authorization for file access (S_DATASET)
Table Maintenance
| Table maintenance using default tools like SM30 (S_TABU_DIS) | |
|---|---|
|
Activity (ACTVT) |
03 (Display) |
|
Auth. group (DICBERCLS) |
ZASE |
Table: Table maintenance using default tools like SM30 (S_TABU_DIS)
_EN.png)
Figure: Table maintenance using default tools like SM30 (S_TABU_DIS)
Note:
For SAP® versions of the base release 700 and higher a new authorization object S_TABU_NAM is available (see SAP® note 1481950). This object also allows you to restrict the access on table level below or alongside an authorization group.
Note:
Using the SmartExporter authorization profiles you can define which tables the SmartExporter end user may access complementary to SmartExporter customized settings for the SAP® authorization check. This may be useful if you do not want to alter existing S_TABU_DIS roles but prefer to create dedicated authorizations for tables with your own authorization object.
With the deployment of the SmartExporter SAP® components 7.0.0004 the authorization object S_USER_GRP was added to allow the assignment of roles to the SmartExporter profile.
User master maintenance: User groups
| User master maintenance: User groups (S_USER_GRP) | |
|---|---|
| User group in user master maintenance (CLASS) | * |
| Activity (ACTVT) | 03 (Display) |
Table: Authorization user master maintenance: User groups (S_USER_GRP)
Note:
The attribute for user group has to be defined according to your requirements on an individual basis.
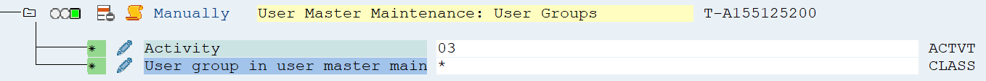
Figure: Authorization for user groups (S_USER_GRP)